Buy options
5.11 CHFPlease check product and platform compatibility before placing an order
All pictures shown are for illustration purpose only. Actual product may slightly vary due to product enhancement or other reasons.
TOTPRadius user license
About TOTPRadius
TOKEN2 TOTPRadius provides the RADIUS RFC-2865 for TOTP RFC-6238 based authentication. With TOTPRadius you can integrate a large variety of third-party products and systems with multifactor authentication. It works with numerous products and services like Cisco Meraki, Citrix XenApp/XenDesktop, VMWare View, and many others that provide support for RADIUS servers to validate the second factor for user authentication.
TOTPRadius user licenses are per-user and perpetual. Perpetual licenses do not expire, so you can continue to use the appliance as long as you want. Currently, these licenses are including access to product updates within the same version branch and regular technical support.
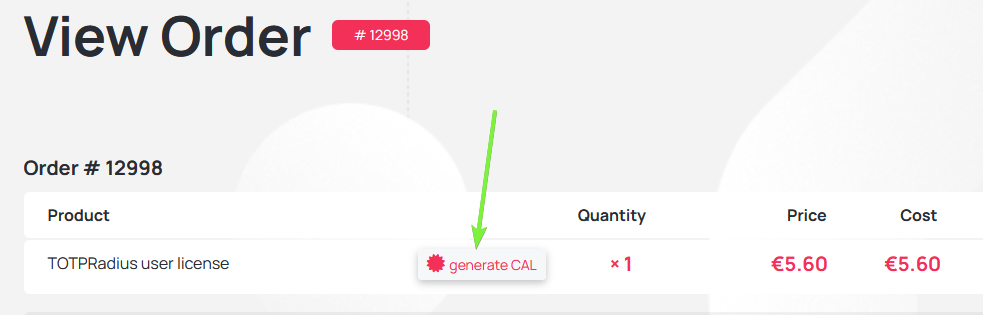
How to generate the license key
After completing the purchase you will receive an email containing the order URL. To generate the TOTPRadius user licenses, click on the "generate CAL" button on the order page and provide the Host ID. The license key will be generated and sent to your email address.
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.






