Using Token2 FIDO2 Security keys for Linux local authentication
 Security keys significantly increase the security level of any solution. On Linux, users can authenticate themselves with the security key thanks to the pam_u2f PAM module.
A one-time registration is needed so that the PAM module knows which public keys are valid for a user. After this, users can authenticate themselves by pressing the key on the USB device.
Security keys significantly increase the security level of any solution. On Linux, users can authenticate themselves with the security key thanks to the pam_u2f PAM module.
A one-time registration is needed so that the PAM module knows which public keys are valid for a user. After this, users can authenticate themselves by pressing the key on the USB device.This guide covers how to secure a local Linux login using Token2 FIDO2 Security Keys. The commands in the guide are for an Ubuntu (or Ubuntu-based) system, but the instructions can be adapted for any distribution of Linux.
Requirements:
• A Token2 FIDO security key with a PIN set• Any of the latest releases of Ubuntu
Installing the required Software
1) Open Terminal2) Run: sudo apt-get update
3) Run: sudo apt-get install libpam-u2f
In Ubuntu, MFA can be used in two authentication scenarios:
a) As a second factor after entering your login and password in the form of touching the token (2FA).
b) As a replacement for entering a password with a PIN code and touching the token (Passwordless).
Setup 2FA
1) Open Terminal2) Run the command:
$ mkdir -p ~/.config/Token2
3) Plug in the security key
4) Run the command:
$ pamu2fcfg > ~/.config/Token2/u2f_keys
Touch the key when the key's light blinks. This will add your FIDO key to the list of accepted security keys.
5) Run the command:
$ sudo mkdir -p /etc/Token2
6) Run the command:
$ sudo mv ~/.config/Token2/u2f_keys /etc/Token2/u2f_keys
7) Run the command:
$ sudo nano /etc/pam.d/common-auth
8) Append line:
auth sufficient pam_u2f.so authfile=/etc/Token2/u2f_keys
9) Save changes to the /etc/pam.d/common-auth file.
Save the file and DO NOT CLOSE THE FILE - CONFIRM that the deployment was successful (see below).
10) Check that a touch is requested when the user logs in by running the command:
$ su fidouser
Setup Passwordless
1) Open Terminal2) Run the command:
$ pamu2fcfg -u username > /tmp/u2f_mappings
Please note that if the command is entered without the username parameter, a configuration file will be created for the current user.
Touch the key when the key's light blinks. This will add your FIDO key to the list of accepted security keys.
3) The result should be a file with similar content:
$ cat /tmp/u2f_mappings
fidouser: hOzdi1ekgoVWLEzQH20uWJmoA3Dwno53zd2WCvlApHwfMVp/zz3+awUbeCL0E3pe,jzL+t6w7vhBgR2wwO+61/g8aliGNbDUpYZj6mxLXain4F1bQB0rvnwzP3n+n/GIXUp5Oiui0Du7/aKP/pE27PQ==,es256,+presence
4) Run the command:
$ sudo mv /tmp/u2f_mappings /etc/Token2/u2f_mappings
5) Run the command:
$ sudo nano /etc/pam.d/common-auth
6) Append line:
auth sufficient pam_u2f.so authfile=/etc/Token2/u2f_mappings cue pinverification=1
7) Save changes to the /etc/pam.d/common-auth file.
Save the file and DO NOT CLOSE THE FILE - CONFIRM that the deployment was successful (see below).
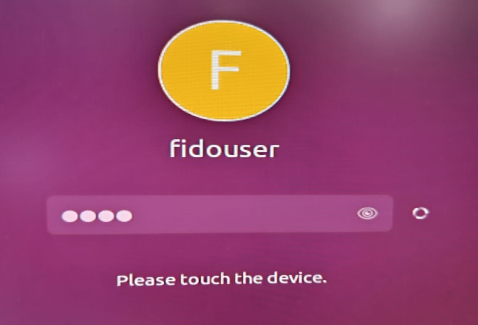
8) Check if a PIN is requested when the user logs in by running the command:
$ su fidouser
Please enter the PIN:
Please touch the device.
9) Check the GUI login:

Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
